- Home
- Products
- InsightIDR
- Features
- Network Traffic Analysis
InsightIDR Feature
Network Traffic Analysis
It’s the end of darkspaces and known unknowns
The Insight platform’s Network Sensor unlocks critical network visibility and detection coverage, alongside data from the rest of your environment. With the lightweight sensor in place, you can quickly recognize suspicious activity on the network. While other network monitoring tools can create a lot of noise, InsightIDR’s curated intrusion detection system (IDS) zeros in on real threats. For strong forensics and investigations, you can access additional network metadata to understand the full scope of activity.
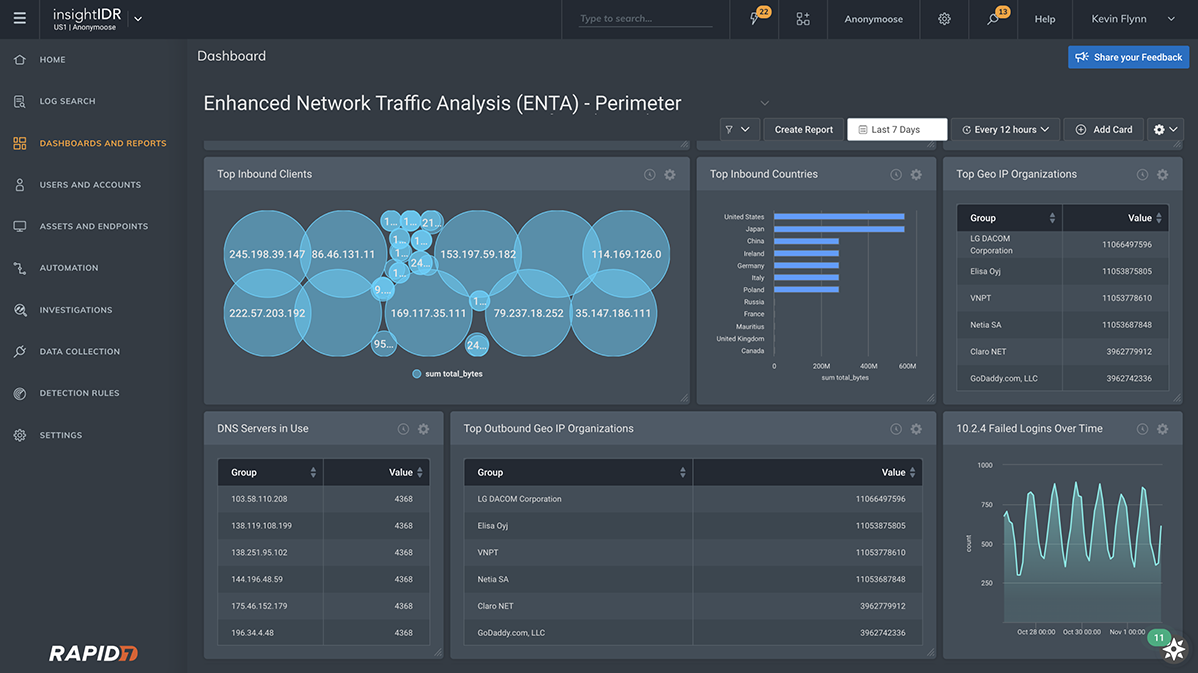

Illuminate your network, accelerate detection, fuel investigations
You know every device, every user on the network leaves a traffic trail. This data is especially difficult for attackers to mess with. When you need to retrace the steps of an attacker across systems and applications, start here. With the Insight platform’s lightweight Network Sensor in place, you’ll have continuous visibility everywhere and quickly recognize suspicious activity.Say goodbye to blind spots
Many security teams admit to having blind spots. Enhanced Network Traffic Analysis (ENTA) helps eliminate them by providing detailed traffic metadata (both at the edge, and inside the network), in an easy to consume, human-readable format. With attribution at the user level, it's easy to quickly build a snapshot of who's on your network and what they're doing.